As highlighted in SAP Security notes, the urgency of the ‘Rapid Reset Attack’ vulnerability cannot be overstated. This article will delve into this critical issue, elucidate its impact on SAP systems, and provide actionable steps to thwart these debilitating threats.

What is a ‘Rapid Reset Attack’?
‘Rapid Reset Attacks’ send an enormous amount of cancellation requests in rapid-fire succession. These commands can bypass a server’s rate limits, putting a system-breaking strain on the device’s resources because opening and closing streams require few resources from the client— but can overload the server side. This denial-of-service attack initiates hundreds of thousands of HTTP/2 streams and rapidly cancels them, at scale, over an established connection. With these reset streams rapidly flowing, threat actors overwhelm websites and knock them offline. When these attacks were aimed at Google’s cloud infrastructure in 2023, they peaked at 398 million requests per second (RPS); the ones that struck AWS and Cloudflare exceeded a volume of 155 million and 201 million RPS, respectively.
The ‘Rapid Reset Attack’ is cataloged under CVE-2023-44487 and said to be exploited publicly ‘in the field.’ To understand this better, we must realize the Hypertext Transfer Protocol (HTTP) and its different versions.
Anyone who has ever used an internet browser knows the HTTP protocol. However, it may not be widely known that it comes in different versions. That may not be important for the average user, but it is essential for IT personnel.
Root Cause: HTTP/2
HTTP protocol version 1.1 was the main version used everywhere in the internet’s nascent days. HTTP1.1 was released in 1997 and was used by all and propagated right along with the global growth of the internet. Though widely accepted and used, it had some flaws. The 1.1 version of the protocol was limited. It had issues when handling multiple requests over a single TCP connection. As the protocol was used more and more and optimizations were added, a negative impact was experienced when processing requests between the HTTP client and server. These efficiency issues were addressed and released in version 2 (HTTP/2) in 2015. The main differences are that HTTP/2 is:
- Based on binary protocols, which are more compact and less prone to errors;
- Using multiplexing for parallelization to prevent blocking of requests;
- Using header compression;
- Allowing servers to ‘push’ a response rather than only waiting for clients to ‘pull’ and;
- Doing all this over a single TCP connection.
We want to take a closer look at the’ multiplexing’ part. This means multiple ‘streams’ of data can be opened, containing multiple messages in request/response format. This format works well for efficiency, but it allows an option for HTTP clients to request a server to cancel a previously opened stream. And that is where this vulnerability exists. A client can open a stream and immediately cancel it. This open/cancel function requires minimal resources from the client but can put an enormous strain on the server. This allows a client to be able to open and immediately close vast numbers of streams and, therefore, be able to overload the server side. Hence, the term ‘Rapid Reset’ was used for this attack.
Impact On SAP Components
As stated earlier, the vulnerability was discovered in 2023. SAP has released three security notes that address the issue and recommend action: 3398186, 3389917, and 3410615. According to these warnings, the Internet Communication Manager (ICM) and Web Dispatcher components primarily require patching or disabling HTTP/2 as a workaround. Concretely, this concerns the following components: Web Dispatcher (standalone or embedded variant), NetWeaver ABAP, Web Dispatcher (XS Classic and Advanced), and PowerDesigner. The impact of the ‘Rapid Reset Attack’ on these components can lead to system overload, potential data loss, and service disruption.
It’s important to note that other SAP components, such as NetWeaver Java, SAP Cloud Connector, and SAP Business Objects, are not affected.
How To Fix The ‘Rapid Reset Attack’ Vulnerability
As IT personnel and SAP system administrators, your role in addressing the ‘Rapid Reset Attack’ vulnerability is crucial. By patching SAP systems, you can effectively insulate them from this threat. To determine if your systems are vulnerable, check the ICM and Web Dispatcher versions. Depending on the version, HTTP/2 may be active and vulnerable, necessitating immediate patching.
When patching, bear in mind that you need to patch in different ways:
| Component | How to patch? |
| Web Dispatcher standalone | Patch Web Dispatcher component directly |
| Web Dispatcher embedded NetWeaver ABAP | Patch the kernel of the affected ABAP system. Note that the embedded Web Dispatcher is a part of the ABAP central services instance (ASCS) |
| Web Dispatcher XS Classic / Advanced | Patch the HANA database and runtime components. |
However, another option for patching is to apply a workaround temporarily. This is controlled with the ICM parameter icm/HTTP/support_http2. Setting this to ‘FALSE’ will disable HTTP/2 altogether, rendering the component not vulnerable to the ‘Rapid Reset Attack.’ Checking the workaround can be done with a simple browser check using the developer tools; see below.
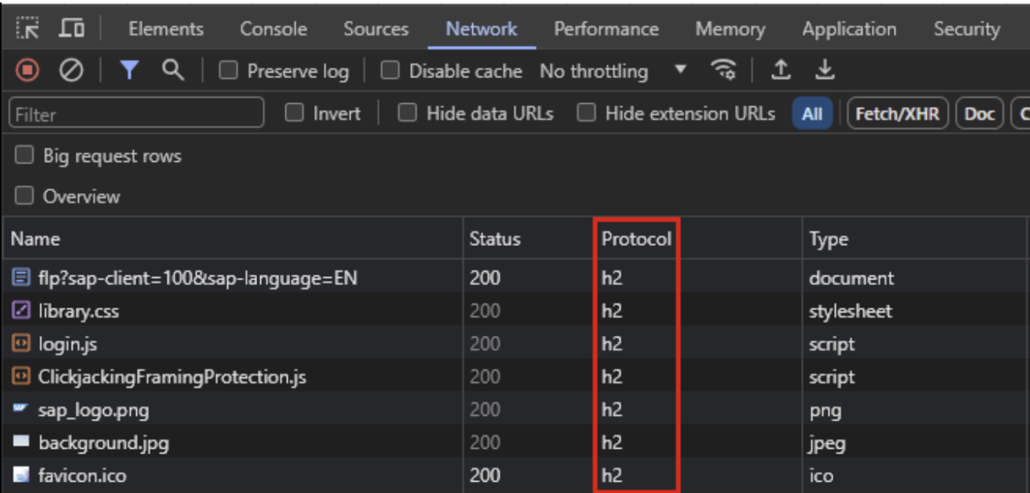
Example: Fiori Launchpad with HTTP/2 active
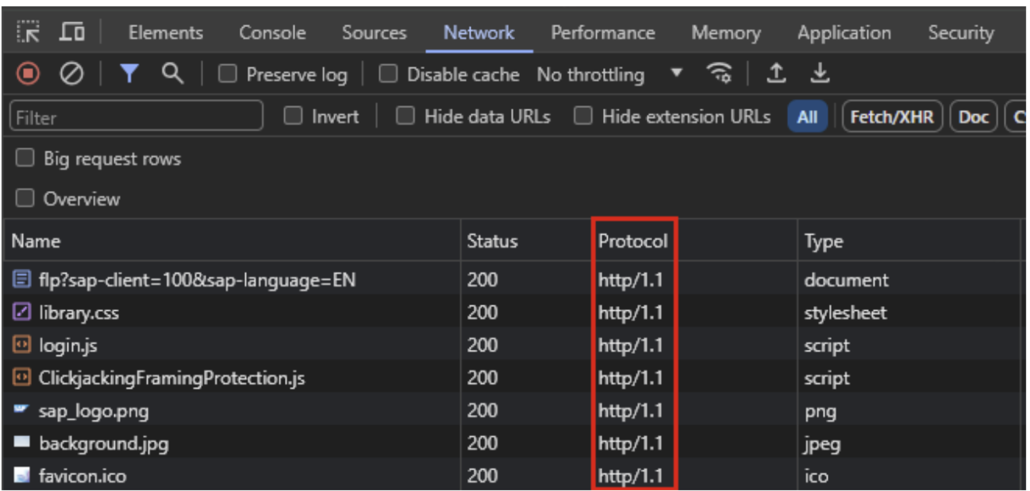
Example: Fiori Launchpad with HTTP/2 inactive > fallback to HTTP 1.1
Conclusion
Manually going through each version for each component in your landscape or setting and checking the workaround takes a lot of time and makes you susceptible to errors. There is a better way to deal with this attack. An automated SAP patch management solution will immediately identify what components need to be fixed in a comprehensive overview. In this manner, checking for parameters, in the case of applying the workaround, is simplified. With a custom baseline setting, all systems can be instantly checked for the correct value. With these solutions, manual labor is kept to a minimum when checking and rechecking to ensure your SAP landscape is secure.
Christoph Nagy
Christoph Nagy has 20 years of working experience within the SAP industry. He has utilized this knowledge as a founding member and CEO at SecurityBridge – a global SAP security provider, serving many of the world’s leading brands and now operating in the U.S. Through his efforts, the SecurityBridge Platform for SAP has become renowned as a strategic security solution for automated analysis of SAP security settings, and detection of cyber-attacks in real-time. Prior to SecurityBridge, Nagy applied his skills as a SAP technology consultant at Adidas and Audi.





